In today's interconnected world, using RemoteIoT behind a firewall on a Mac has become increasingly important for businesses and individuals alike. Whether you're managing IoT devices remotely or ensuring secure network access, this guide provides the tools and knowledge to achieve seamless connectivity. Learn how to use RemoteIoT behind a firewall using your Mac while maintaining optimal security and performance.
As technology evolves, so does the need for secure and efficient remote access solutions. RemoteIoT allows users to interact with IoT devices from anywhere, but doing so behind a firewall adds an extra layer of complexity. This article will help you navigate through the process, ensuring that your setup is both secure and functional.
This guide is tailored for professionals and enthusiasts who want to harness the full potential of RemoteIoT on their Mac devices. Whether you're setting up for personal use or implementing it within an enterprise environment, the information provided here will be invaluable.
Read also:Unlock Productivity With Raspberry Pi Remote Desktop Browser Free
Understanding RemoteIoT and Its Importance
What is RemoteIoT?
RemoteIoT refers to the ability to access and manage Internet of Things (IoT) devices remotely. This technology enables users to control, monitor, and interact with IoT devices regardless of their physical location. For businesses, this means increased efficiency and flexibility in managing IoT infrastructure.
- RemoteIoT simplifies device management.
- It enhances productivity by allowing real-time monitoring.
- It ensures that IoT devices remain operational even when users are offsite.
Why Use RemoteIoT Behind a Firewall?
Using RemoteIoT behind a firewall is crucial for maintaining security and protecting sensitive data. Firewalls act as a barrier between your internal network and external threats, ensuring that unauthorized access is prevented. By configuring RemoteIoT to work behind a firewall, you can enjoy the benefits of remote access without compromising your network's integrity.
Key benefits of using RemoteIoT behind a firewall include:
- Enhanced security through controlled access.
- Protection against unauthorized access and cyberattacks.
- Improved privacy for sensitive IoT data.
Setting Up Your Mac for RemoteIoT
Prerequisites for Using RemoteIoT on a Mac
Before diving into the setup process, ensure your Mac meets the following requirements:
- macOS version 10.14 (Mojave) or later.
- A stable internet connection.
- A firewall configured to allow RemoteIoT traffic.
- Access to your IoT device's management interface.
Having these prerequisites in place will make the setup process smoother and more efficient.
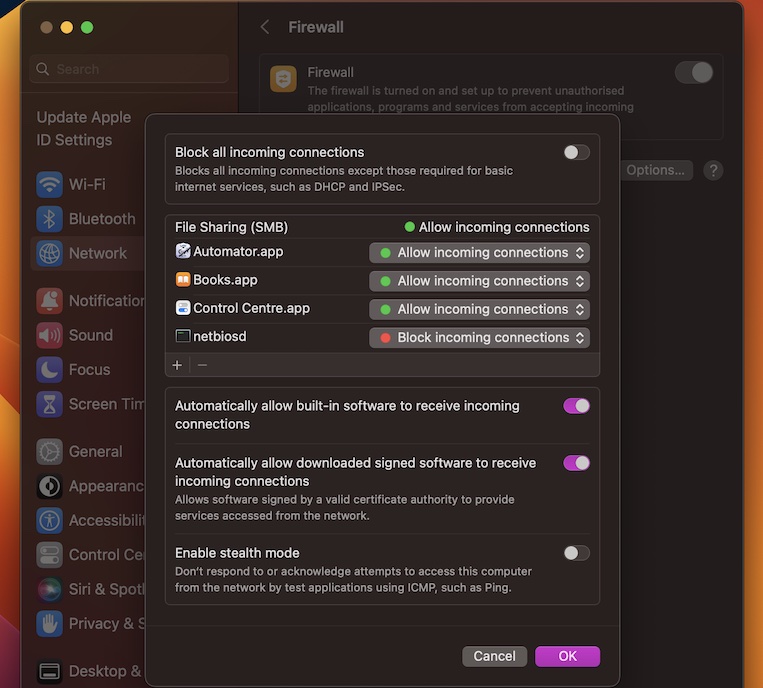
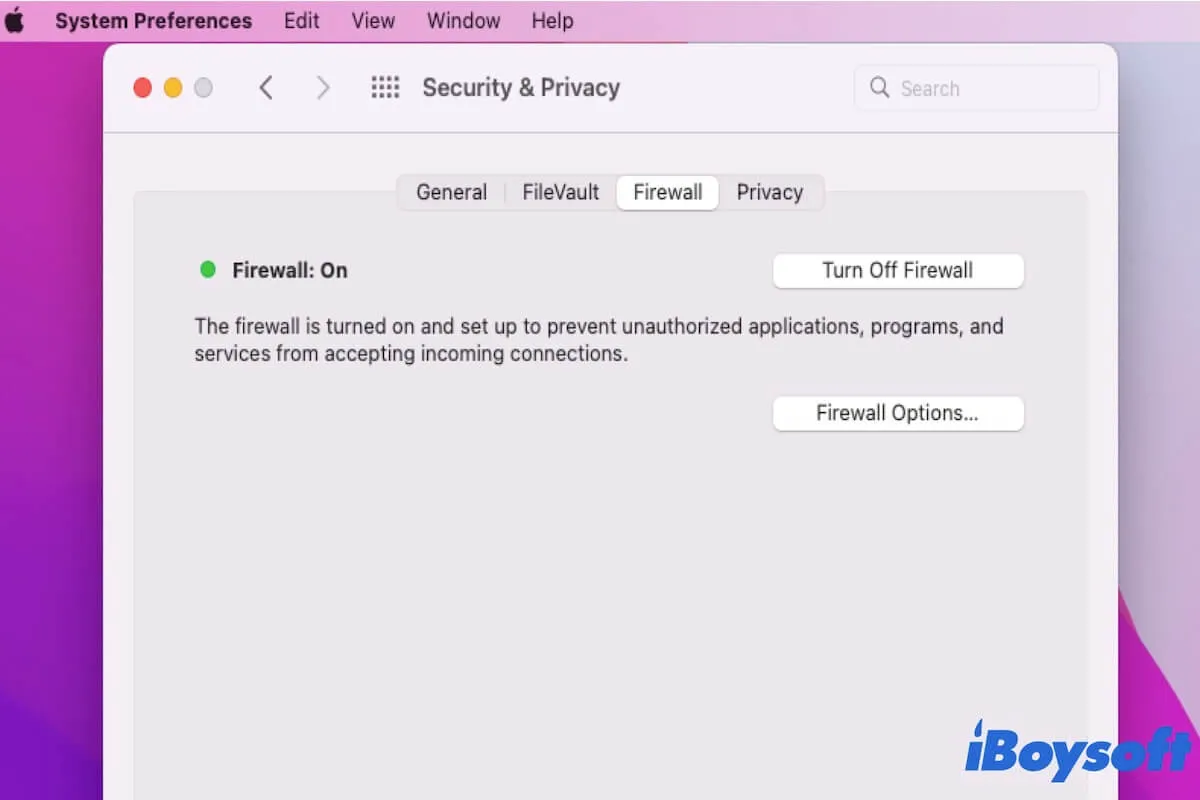
Configuring Firewall Settings for RemoteIoT
Configuring your firewall is essential for allowing RemoteIoT to function properly. Follow these steps to set up your firewall:
Read also:Unveiling Movierulzs Com 2023 Your Ultimate Guide To Streaming Movies
- Identify the ports used by RemoteIoT. Common ports include 80, 443, and 8080.
- Log in to your firewall management interface.
- Create a rule allowing inbound and outbound traffic on the specified ports.
- Test the configuration to ensure connectivity.
By properly configuring your firewall, you enable secure communication between your Mac and IoT devices while maintaining network security.
Steps to Use RemoteIoT Behind Firewall Using Mac
Step 1: Install Necessary Software
To use RemoteIoT on your Mac, you'll need to install specific software. Follow these steps:
- Download the RemoteIoT client application from the official website.
- Install the application by following the on-screen instructions.
- Verify the installation by launching the application.
Using official software ensures compatibility and security, reducing the risk of vulnerabilities.
Step 2: Configure Network Settings
Configuring your Mac's network settings is crucial for RemoteIoT functionality. Here's how:
- Go to System Preferences > Network.
- Select your active network connection.
- Click Advanced and configure proxy settings if required.
Proper network configuration ensures that RemoteIoT can communicate effectively with your IoT devices.
Step 3: Connect to IoT Devices
Connecting to your IoT devices involves several steps:
- Launch the RemoteIoT application.
- Enter the device's IP address or hostname.
- Authenticate using the provided credentials.
Once connected, you can begin managing your IoT devices remotely.
Troubleshooting Common Issues
Firewall Blocking RemoteIoT Traffic
If your firewall is blocking RemoteIoT traffic, follow these troubleshooting steps:
- Check firewall logs for denied connections.
- Verify that the correct ports are open.
- Temporarily disable the firewall to test connectivity.
Addressing firewall-related issues promptly ensures uninterrupted RemoteIoT functionality.
Connection Problems with IoT Devices
Connection issues with IoT devices can arise due to various reasons. Consider the following solutions:
- Ensure the IoT device is online and reachable.
- Check for network connectivity issues on your Mac.
- Restart both the device and the RemoteIoT application.
Resolving connection problems quickly minimizes downtime and maximizes productivity.
Security Best Practices for RemoteIoT
Implementing Strong Authentication
Strong authentication is vital for securing RemoteIoT access. Follow these best practices:
- Use complex passwords or passphrases.
- Enable two-factor authentication (2FA) whenever possible.
- Regularly update credentials to prevent unauthorized access.
By enforcing strong authentication, you protect your IoT devices from potential breaches.
Regularly Updating Software
Keeping your RemoteIoT software up to date is essential for maintaining security. Updates often include:
- Security patches addressing vulnerabilities.
- Performance improvements and bug fixes.
- New features enhancing functionality.
Regular updates ensure that your setup remains secure and reliable.
Advanced Configurations for RemoteIoT
Using SSH Tunnels for Secure Connections
SSH tunnels provide an additional layer of security for RemoteIoT connections. To set up an SSH tunnel:
- Install an SSH client on your Mac.
- Configure the tunnel to forward traffic to your IoT device.
- Test the connection to ensure secure communication.
SSH tunnels encrypt data transmitted between your Mac and IoT devices, enhancing overall security.
Implementing Virtual Private Networks (VPNs)
VPNs offer another method for securing RemoteIoT connections. Benefits include:
- Encrypted communication channels.
- Improved privacy and anonymity.
- Access to restricted networks.
Integrating a VPN with RemoteIoT ensures that your data remains protected while accessing IoT devices remotely.
Conclusion and Call to Action
In conclusion, using RemoteIoT behind a firewall on a Mac requires careful planning and configuration. By following the steps outlined in this guide, you can achieve secure and reliable remote access to your IoT devices. Remember to prioritize security through strong authentication, regular updates, and advanced configurations like SSH tunnels and VPNs.
We invite you to share your experiences and insights in the comments section below. Your feedback helps us improve and provides valuable information to other readers. Additionally, explore our other articles for more tips and tricks on managing IoT devices and enhancing network security.
Table of Contents