In today's interconnected world, mastering remote IoT VPC SSH AWS has become a critical skill for IT professionals and organizations aiming to enhance secure connectivity. The rise of Internet of Things (IoT) devices has transformed how businesses operate, creating a need for secure and efficient remote access solutions. By leveraging AWS VPC and SSH, organizations can build robust infrastructures that safeguard their networks and data.
As more companies adopt cloud computing and IoT technologies, the demand for secure remote access grows exponentially. AWS provides a powerful platform to manage IoT devices and establish secure connections through its Virtual Private Cloud (VPC) and Secure Shell (SSH) protocols. This guide explores the essential steps and best practices for mastering remote IoT VPC SSH AWS configurations.
Whether you're a seasoned IT professional or just starting your journey in cloud computing, this comprehensive guide will equip you with the knowledge and tools to create secure and scalable remote connectivity solutions. Let's dive into the world of AWS VPC and SSH to unlock the full potential of IoT deployments.
Read also:Move Rolz The Ultimate Guide To Understanding And Mastering Your Moves
Table of Contents
- Introduction to AWS VPC
- Understanding SSH
- IoT and Remote Connectivity
- Configuring VPC for Remote IoT
- Securing SSH Connections
- Best Practices for Remote IoT
- Troubleshooting Common Issues
- Scaling Remote Connectivity
- Case Studies
- Conclusion
Introduction to AWS VPC
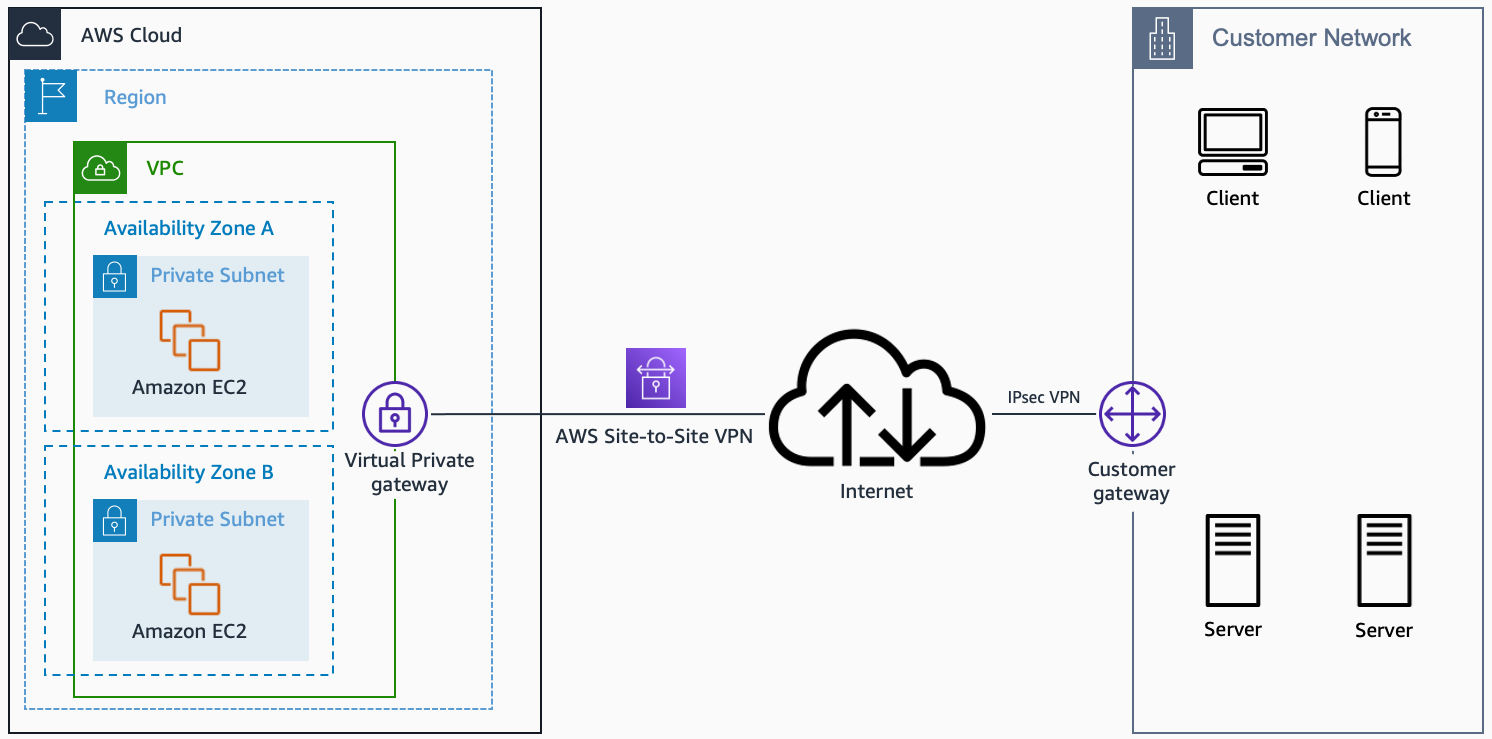
AWS Virtual Private Cloud (VPC) is a foundational component of AWS infrastructure that enables users to create isolated virtual networks within the AWS Cloud. This feature is crucial for mastering remote IoT VPC SSH AWS configurations. A VPC allows organizations to define their own IP address ranges, subnets, and route tables, providing granular control over network traffic.
VPCs play a vital role in securing IoT devices by isolating them from public internet access while still allowing controlled remote access. By configuring security groups and network access control lists (NACLs), organizations can define precisely which devices and services can communicate with each other.
With AWS VPC, businesses can build scalable and secure environments tailored to their specific needs. This flexibility is essential for managing IoT deployments where devices may be spread across multiple locations and require consistent connectivity.
Understanding SSH
Secure Shell (SSH) is a cryptographic protocol used to secure communications between devices over an unsecured network. When mastering remote IoT VPC SSH AWS, understanding SSH is fundamental to establishing secure connections. SSH encrypts all data transmitted between devices, ensuring confidentiality and integrity.
SSH offers several key benefits for IoT deployments:
- Encryption: Protects data in transit from unauthorized access.
- Authentication: Ensures only authorized users can access devices.
- Command Execution: Allows administrators to remotely execute commands on IoT devices.
By integrating SSH with AWS VPC, organizations can create a secure tunnel for remote access to IoT devices, minimizing the risk of unauthorized access or data breaches.
Read also:The Richest Person In Kenya 2025 Unveiling Wealth And Influence
IoT and Remote Connectivity
The Internet of Things (IoT) has revolutionized how businesses and individuals interact with technology. IoT devices are now deployed in various industries, from healthcare to manufacturing, requiring secure and reliable remote connectivity solutions. Mastering remote IoT VPC SSH AWS is essential for ensuring these devices operate efficiently and securely.
Remote connectivity in IoT involves enabling devices to communicate with centralized servers or other devices over the internet. This process requires robust security measures to prevent unauthorized access and protect sensitive data. AWS VPC and SSH provide the tools needed to secure these connections, ensuring data integrity and device reliability.
As IoT deployments continue to grow, the importance of secure remote access will only increase. By leveraging AWS VPC and SSH, organizations can stay ahead of the curve and maintain a competitive edge in the market.
Configuring VPC for Remote IoT
Configuring a VPC for remote IoT devices involves several steps to ensure secure and efficient connectivity. Below, we outline the key processes involved in setting up an AWS VPC for IoT deployments.
Step 1: Create a VPC
The first step in mastering remote IoT VPC SSH AWS is creating a VPC. This involves defining the IP address range and subnet configurations for your network. When creating a VPC, consider the following:
- Define a CIDR block that accommodates your expected number of devices.
- Choose an appropriate region based on your deployment requirements.
- Enable DNS hostnames and DNS resolution for easier device management.
Creating a VPC lays the foundation for secure IoT deployments, providing a controlled environment for device communication.
Step 2: Configure Subnets
Once your VPC is created, the next step is configuring subnets. Subnets allow you to segment your network into smaller, more manageable parts. This is particularly useful for IoT deployments where devices may have different security and connectivity requirements.
When configuring subnets, consider the following best practices:
- Create public and private subnets to separate internet-facing devices from internal ones.
- Use route tables to define how traffic flows between subnets.
- Implement network access control lists (NACLs) to restrict traffic based on IP addresses and protocols.
Proper subnet configuration is essential for maintaining secure and efficient IoT networks.
Securing SSH Connections
Securing SSH connections is a critical aspect of mastering remote IoT VPC SSH AWS. While SSH provides robust encryption and authentication mechanisms, additional measures are necessary to ensure maximum security. Below are some best practices for securing SSH connections:
- Use strong, unique SSH keys for authentication instead of passwords.
- Disable root login to prevent unauthorized access to critical systems.
- Limit SSH access to specific IP addresses using security groups or NACLs.
- Regularly update SSH software to patch vulnerabilities and improve security.
By implementing these measures, organizations can significantly reduce the risk of unauthorized access and data breaches in their IoT deployments.
Best Practices for Remote IoT
To master remote IoT VPC SSH AWS configurations, it's essential to follow best practices that enhance security, scalability, and efficiency. Below are some key practices to consider:
- Regularly monitor network traffic for unusual activity or potential security threats.
- Implement automated backups for IoT device configurations and data.
- Use AWS CloudWatch to monitor and log SSH activity for auditing purposes.
- Regularly review and update security policies to adapt to evolving threats.
Adhering to these best practices ensures that your IoT deployments remain secure and efficient, even as they grow in complexity and scale.
Troubleshooting Common Issues
Even with the best planning and configuration, issues may arise when mastering remote IoT VPC SSH AWS. Below are some common challenges and their solutions:
- Connection Failures: Verify SSH key configurations and ensure security groups allow SSH traffic.
- Slow Performance: Optimize subnet configurations and use AWS Direct Connect for faster connectivity.
- Unauthorized Access: Review SSH logs and update security policies to prevent future incidents.
By understanding and addressing these common issues, organizations can maintain stable and secure IoT deployments.
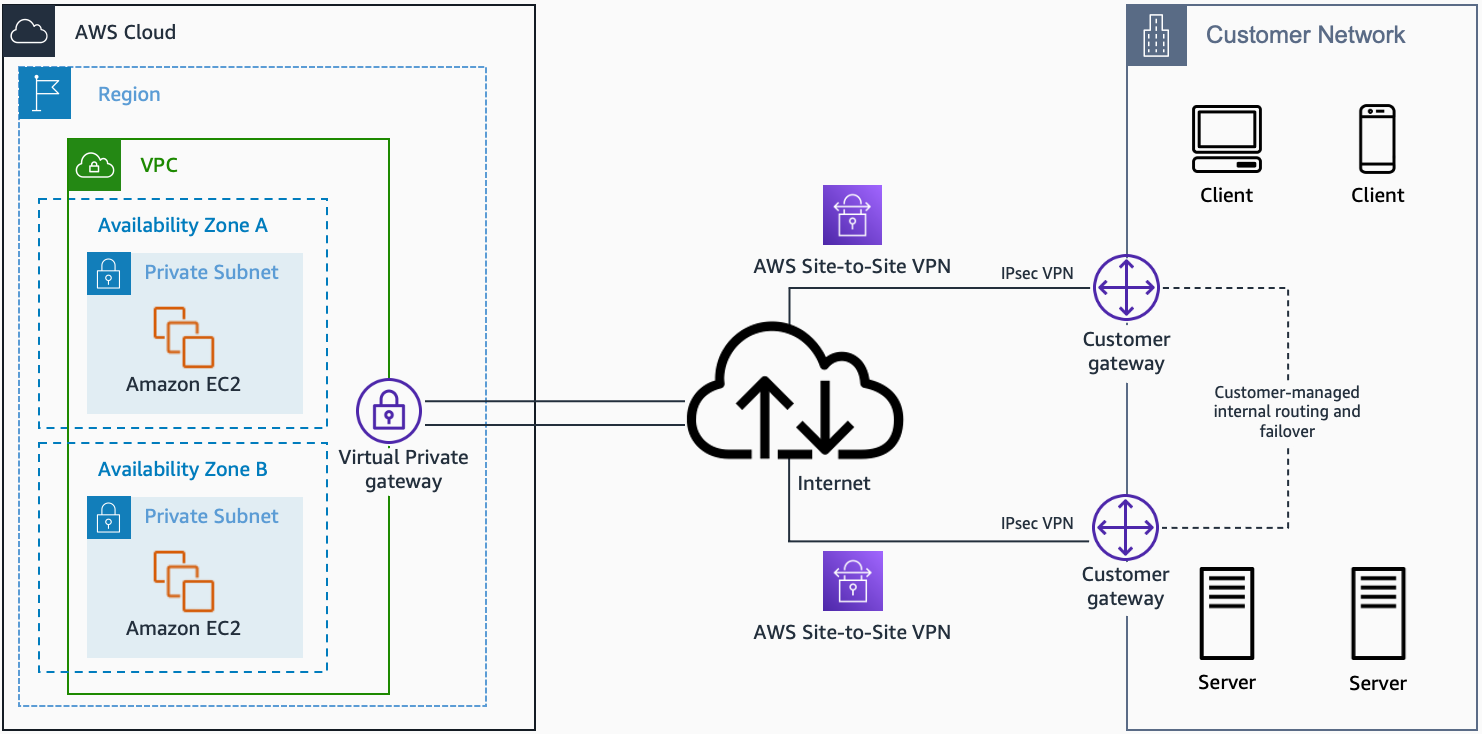
Scaling Remote Connectivity
As IoT deployments grow, scaling remote connectivity becomes increasingly important. AWS provides several tools and services to help organizations scale their IoT VPC SSH configurations effectively. Below are some strategies for scaling remote connectivity:
- Use AWS Auto Scaling to automatically adjust resources based on demand.
- Implement load balancers to distribute traffic across multiple devices.
- Utilize AWS IoT Core for managing large-scale IoT device fleets.
Scaling remote connectivity ensures that your IoT deployments remain efficient and responsive, even as the number of devices increases.
Case Studies
Several organizations have successfully implemented remote IoT VPC SSH AWS configurations to enhance their operations. Below are two examples:
- Healthcare Provider: A healthcare provider used AWS VPC and SSH to secure remote access to IoT medical devices, ensuring patient data remained confidential and compliant with regulations.
- Manufacturing Company: A manufacturing company leveraged AWS IoT Core and SSH to monitor and manage production line devices remotely, improving efficiency and reducing downtime.
These case studies demonstrate the versatility and effectiveness of AWS VPC and SSH in securing IoT deployments across various industries.
Conclusion
Mastering remote IoT VPC SSH AWS is essential for organizations seeking to enhance secure connectivity in their IoT deployments. By leveraging AWS VPC and SSH, businesses can create robust and scalable infrastructures that protect their networks and data. This guide has explored the key steps and best practices for configuring and securing remote IoT environments, providing a solid foundation for success.
We invite you to share your thoughts and experiences in the comments section below. Additionally, consider exploring other resources on our site to deepen your understanding of cloud computing and IoT technologies. Together, let's build a more secure and connected future.