In today's interconnected world, secure remote login IoT password management is more critical than ever. As the Internet of Things (IoT) continues to expand, ensuring the security of your devices has become a top priority. With billions of devices connected globally, the risks of unauthorized access and data breaches are on the rise. Understanding how to secure your IoT devices is essential for both individuals and businesses.
IoT technology brings convenience and efficiency to our lives, from smart homes to industrial automation. However, this convenience comes with significant security challenges. Devices connected to the internet are vulnerable to cyberattacks, making it imperative to implement robust security measures. A secure remote login IoT password strategy is one of the most effective ways to safeguard your devices.
This comprehensive guide will walk you through the importance of securing IoT devices, best practices for password management, and strategies to enhance your device security. Whether you're a tech enthusiast or a business owner, this guide will equip you with the knowledge to protect your IoT ecosystem effectively.
Read also:9x Movies Your Ultimate Guide To Streaming And Downloading Movies
Table of Contents
- The Importance of Secure Remote Login IoT Password
- Common Risks in IoT Security
- Password Best Practices for IoT Devices
- Implementing Multi-Factor Authentication
- The Role of Encryption in IoT Security
- Enhancing Network Security for IoT Devices
- Effective IoT Device Management
- Regular Software Updates and Patching
- Tools and Technologies for IoT Security
- Conclusion and Next Steps
The Importance of Secure Remote Login IoT Password
In the realm of IoT, a secure remote login IoT password serves as the first line of defense against unauthorized access. According to a report by Gartner, the number of IoT devices is projected to reach over 25 billion by 2025. Each of these devices represents a potential entry point for cybercriminals if not properly secured.
A strong password acts as a gatekeeper, ensuring that only authorized users can access your devices. Weak or default passwords are one of the most common vulnerabilities exploited by hackers. By implementing secure password practices, you can significantly reduce the risk of unauthorized access and data breaches.
Why Password Security Matters in IoT
Password security is crucial because IoT devices often handle sensitive data, such as personal information, financial transactions, and even critical infrastructure controls. A compromised device can lead to data theft, financial loss, and reputational damage. Moreover, a breach in one device can compromise an entire network, making it essential to prioritize security at every level.
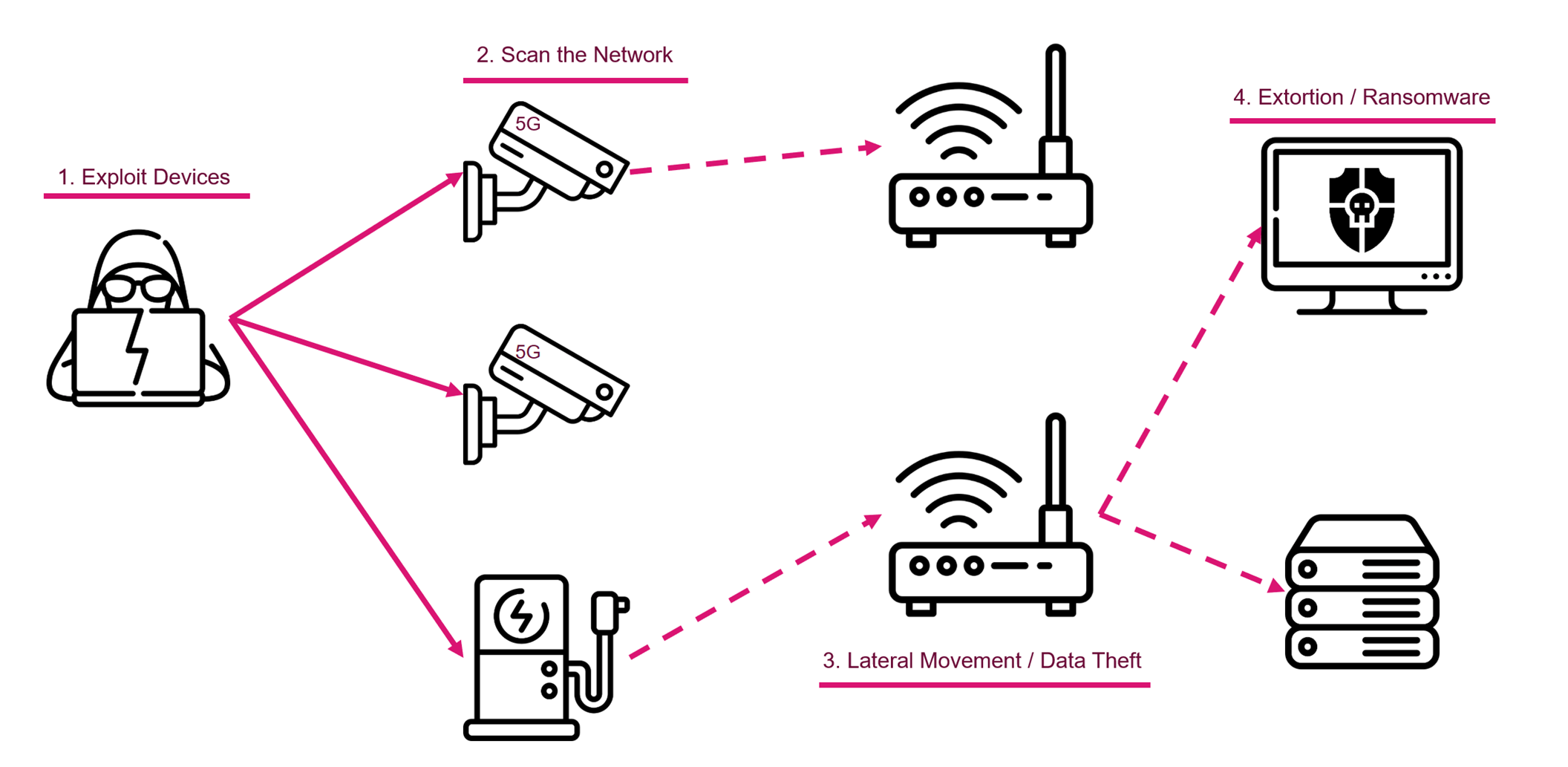
Common Risks in IoT Security
While IoT devices offer numerous benefits, they also introduce several security risks. Understanding these risks is the first step toward mitigating them. Below are some of the most common IoT security challenges:
- Default Passwords: Many IoT devices come with default passwords that are easily guessable or widely known. Failing to change these passwords leaves devices vulnerable to attacks.
- Weak Authentication: Some devices lack robust authentication mechanisms, making it easier for attackers to gain access.
- Unsecured Networks: Devices connected to unsecured or poorly configured networks are at higher risk of being compromised.
- Outdated Software: Devices running outdated firmware or software are more susceptible to vulnerabilities that have been patched in newer versions.
Statistical Insights on IoT Security Risks
According to a recent study by Symantec, 60% of IoT devices are vulnerable to medium or high-severity attacks. Furthermore, 70% of IoT devices do not encrypt data during transmission, leaving sensitive information exposed to interception.
Password Best Practices for IoT Devices
Creating strong, unique passwords is fundamental to securing your IoT devices. Here are some best practices to follow:
Read also:Movierulz 2024 Download Your Ultimate Guide To Safe And Legal Movie Downloads
- Use Complex Passwords: Incorporate a mix of uppercase and lowercase letters, numbers, and special characters.
- Avoid Reusing Passwords: Use unique passwords for each device to prevent a single breach from compromising multiple devices.
- Change Default Passwords: Always change the default passwords provided by manufacturers immediately after setup.
- Enable Password Managers: Consider using a password manager to generate and store complex passwords securely.
Creating a Strong IoT Password
A strong IoT password should be at least 12 characters long and include a combination of letters, numbers, and symbols. Avoid using easily guessable information such as birthdays or common phrases. Instead, opt for random combinations that are difficult to predict.
Implementing Multi-Factor Authentication
While strong passwords are essential, they are not foolproof. Adding an extra layer of security through multi-factor authentication (MFA) can significantly enhance protection. MFA requires users to provide two or more verification factors to gain access, such as a password and a one-time code sent to their mobile device.
Benefits of Multi-Factor Authentication
Implementing MFA offers several advantages, including:
- Reduced risk of unauthorized access
- Enhanced user authentication
- Improved overall security posture
The Role of Encryption in IoT Security
Encryption plays a vital role in securing data transmitted between IoT devices. By encrypting data, you ensure that even if it is intercepted, it remains unreadable to unauthorized parties. There are several encryption protocols available, such as AES (Advanced Encryption Standard) and TLS (Transport Layer Security), which can be implemented to protect your IoT ecosystem.
How Encryption Works
Encryption converts plain text into cipher text using complex algorithms. Only those with the correct decryption key can access the original data. This ensures that sensitive information remains secure during transmission and storage.
Enhancing Network Security for IoT Devices
Securing the network your IoT devices are connected to is equally important. A secure network reduces the risk of unauthorized access and data breaches. Below are some strategies to enhance network security:
- Segment Networks: Isolate IoT devices on a separate network to limit potential damage in case of a breach.
- Use Firewalls: Deploy firewalls to monitor and control incoming and outgoing network traffic.
- Implement VLANs: Use virtual local area networks (VLANs) to further segment and secure your network.
Network Security Best Practices
In addition to the strategies mentioned above, regularly updating network firmware and conducting security audits can help identify and address potential vulnerabilities.
Effective IoT Device Management
Managing IoT devices effectively is crucial for maintaining their security. This includes monitoring device activity, implementing access controls, and ensuring timely updates. Centralized device management platforms can simplify these tasks and provide greater visibility into your IoT ecosystem.
Key Features of IoT Device Management Platforms
Some of the key features to look for in an IoT device management platform include:
- Remote monitoring and control
- Automated software updates
- Comprehensive reporting and analytics
Regular Software Updates and Patching
Keeping your IoT devices up to date with the latest software patches is essential for maintaining their security. Manufacturers frequently release updates to address newly discovered vulnerabilities. Failing to apply these updates leaves devices exposed to potential attacks.
Why Regular Updates Are Important
Regular updates not only address security vulnerabilities but also improve device performance and functionality. They ensure that your devices remain compatible with the latest technologies and standards, providing a more secure and reliable user experience.
Tools and Technologies for IoT Security
Several tools and technologies are available to help secure your IoT devices. These range from intrusion detection systems to endpoint protection platforms. Evaluating and selecting the right tools for your needs is crucial for building a robust security infrastructure.
Popular IoT Security Tools
Some of the most popular IoT security tools include:
- IoT Security Framework
- Device Management Platforms
- Network Monitoring Solutions
Conclusion and Next Steps
Securing your IoT devices requires a comprehensive approach that includes strong passwords, multi-factor authentication, encryption, network security, and regular updates. By following the best practices outlined in this guide, you can significantly enhance the security of your IoT ecosystem and protect your devices from potential threats.
We encourage you to take the next step by implementing these strategies in your own environment. Share your thoughts and experiences in the comments below, and don't forget to explore other articles on our site for more valuable insights into IoT security.