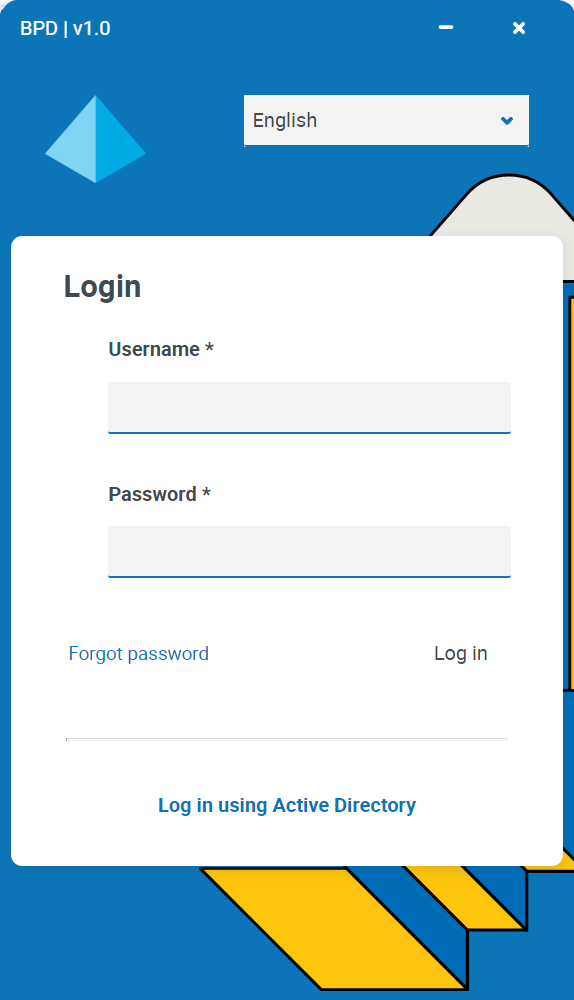
In today's digital age, mastering RemoteIoT desktop login has become a crucial skill for professionals and tech enthusiasts alike. Whether you're managing remote servers, accessing cloud-based platforms, or controlling IoT devices, understanding how to securely log in to RemoteIoT is essential. This guide will walk you through every step, ensuring you're equipped with the knowledge and tools to handle this process effectively.
As more businesses adopt IoT technologies, the demand for secure and efficient remote access solutions continues to grow. RemoteIoT desktop login serves as a bridge between users and their IoT ecosystems, enabling seamless interaction from anywhere in the world. This article aims to provide a detailed, step-by-step approach to mastering this process, ensuring your experience is both secure and hassle-free.
Whether you're a beginner exploring the world of IoT or an experienced professional seeking to refine your skills, this comprehensive guide will cater to your needs. We'll cover everything from the basics of RemoteIoT login to advanced tips and tricks, ensuring you're well-prepared for any challenge that comes your way.
Read also:Comprehensive Guide To Movierulz 2023 Movie Download Everything You Need To Know
Understanding RemoteIoT Desktop Login
What is RemoteIoT Desktop Login?
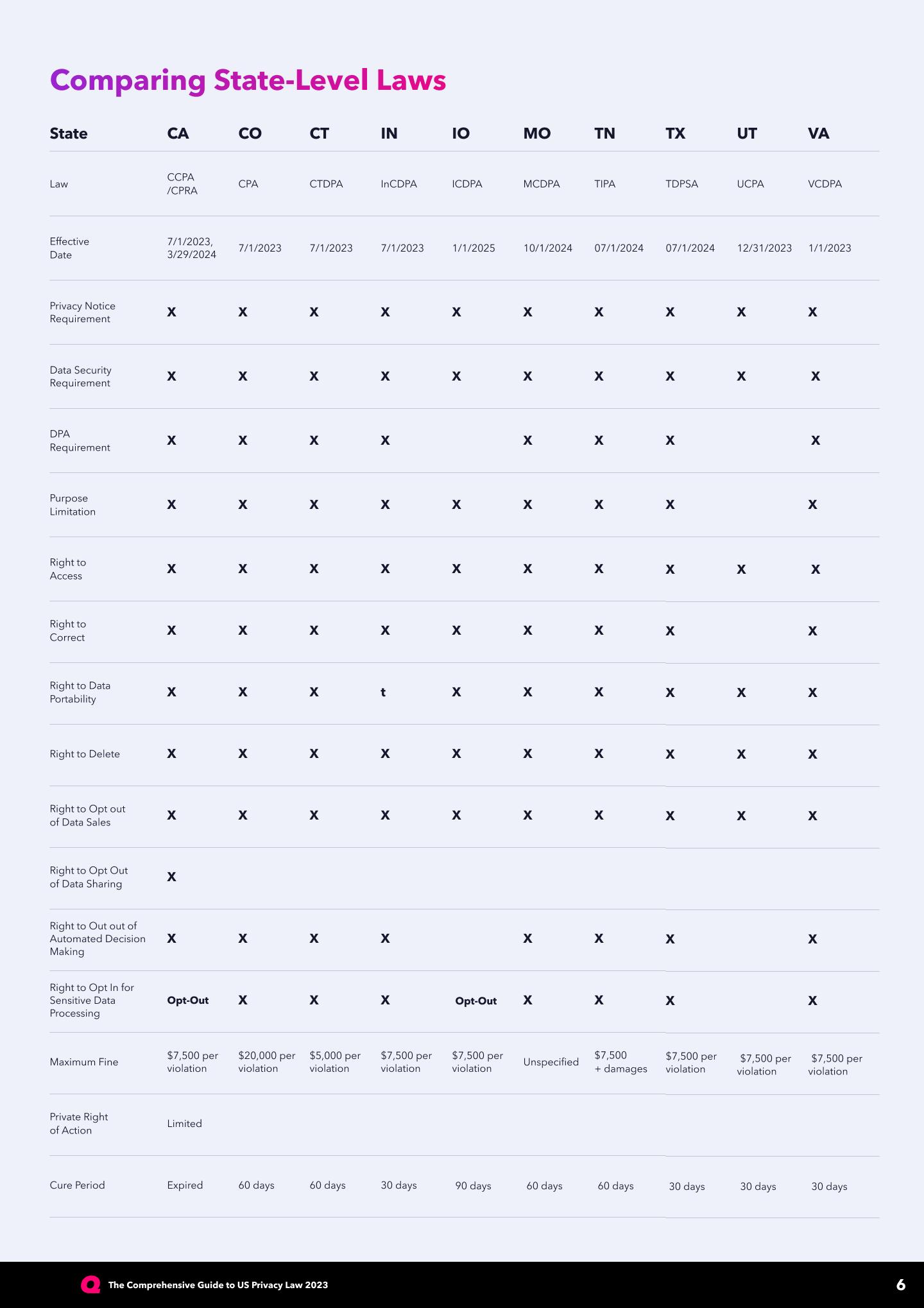
RemoteIoT desktop login refers to the process of securely accessing IoT-enabled devices and platforms remotely. It allows users to manage, monitor, and control their IoT infrastructure from any location, provided they have an internet connection. This functionality is particularly useful for businesses that rely on IoT devices for operations, as it enables real-time monitoring and maintenance.
According to a report by Gartner, the number of IoT devices is expected to surpass 25 billion by 2030, emphasizing the importance of robust remote access solutions. Understanding how to navigate RemoteIoT desktop login is not only about convenience but also about ensuring the security and integrity of your IoT ecosystem.
Key Features of RemoteIoT Login
RemoteIoT desktop login comes with several key features that enhance user experience and security:
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring additional verification steps beyond just a password.
- Device Compatibility: Supports a wide range of devices, ensuring seamless access across platforms.
- Real-Time Monitoring: Allows users to monitor IoT devices in real-time, providing instant updates on performance and status.
- Customizable Dashboards: Users can tailor their dashboards to display the most relevant information for their specific needs.
Steps to Master RemoteIoT Desktop Login
Step 1: Setting Up Your Account
The first step in mastering RemoteIoT desktop login is setting up your account. This involves creating a secure username and password, as well as configuring any additional security settings. It's crucial to choose a strong password that combines uppercase and lowercase letters, numbers, and special characters to enhance security.
For example, a password like "P@ssw0rd2023" is more secure than "password123." Additionally, enabling multi-factor authentication during this stage can significantly reduce the risk of unauthorized access.
Step 2: Downloading the RemoteIoT Client
Once your account is set up, the next step is downloading the RemoteIoT client software. This software acts as the interface between your device and the RemoteIoT platform, enabling secure communication and data transfer. Ensure you download the client from the official website or a trusted source to avoid potential security risks.
Read also:Ssh Raspberry Pi Iot Projects For Beginners A Comprehensive Guide
According to a study by Symantec, over 40% of downloaded software contains malicious code, underscoring the importance of sourcing your downloads from reputable providers.
Step 3: Configuring Security Settings
Configuring security settings is a critical step in mastering RemoteIoT desktop login. This involves setting up firewalls, encrypting data transmissions, and enabling secure protocols such as SSL/TLS. These measures help protect your IoT ecosystem from cyber threats and unauthorized access.
For instance, enabling SSL/TLS encryption ensures that all data transmitted between your device and the RemoteIoT platform is encrypted, making it difficult for attackers to intercept and decipher sensitive information.
Best Practices for Secure RemoteIoT Login
Implementing Strong Password Policies
Implementing strong password policies is one of the most effective ways to enhance the security of your RemoteIoT desktop login. This includes regularly updating passwords, avoiding common phrases or dictionary words, and using password managers to generate and store complex passwords.
Research by Microsoft indicates that weak passwords account for over 80% of hacking-related breaches, highlighting the importance of adopting robust password practices.
Regularly Updating Software and Firmware
Regularly updating your RemoteIoT client software and associated firmware is essential for maintaining security and functionality. Updates often include patches for known vulnerabilities, performance improvements, and new features that enhance user experience.
For example, the 2021 Log4j vulnerability highlighted the importance of keeping software up to date, as outdated versions can expose systems to significant risks.
Monitoring Login Attempts
Monitoring login attempts is another best practice for securing your RemoteIoT desktop login. This involves reviewing logs for any suspicious activity, such as multiple failed login attempts or logins from unfamiliar locations. Implementing tools like intrusion detection systems (IDS) can automate this process, providing real-time alerts for potential security breaches.
Common Challenges and Solutions
Handling Forgotten Passwords
One common challenge users face is forgetting their RemoteIoT desktop login credentials. To address this, most platforms offer password recovery options, such as sending a reset link to your registered email address or answering security questions. It's important to keep your recovery information up to date to ensure smooth access in case of emergencies.
Dealing with Connectivity Issues
Connectivity issues can hinder your ability to log in to RemoteIoT desktop. These problems may stem from network outages, server downtime, or configuration errors. To mitigate these challenges, ensure your internet connection is stable, verify server status through official channels, and consult documentation for troubleshooting tips.
Managing Multiple Devices
Managing multiple devices can be overwhelming, especially when each requires unique login credentials. Utilizing tools like single sign-on (SSO) or centralized authentication systems can simplify this process, allowing users to access all their devices with a single set of credentials while maintaining security.
Advanced Tips for Mastering RemoteIoT Login
Utilizing Automation Tools
Automation tools can significantly enhance the efficiency of RemoteIoT desktop login processes. These tools can automate repetitive tasks, such as logging in to multiple devices or performing routine maintenance checks, freeing up time for more critical activities.
For instance, tools like Ansible or Puppet can be configured to manage RemoteIoT logins across a network of devices, ensuring consistency and reducing the risk of human error.
Exploring API Integration
Exploring API integration is another advanced tip for mastering RemoteIoT desktop login. APIs enable seamless communication between different systems and platforms, allowing users to extend the functionality of their RemoteIoT setup. This can include integrating with third-party applications for enhanced monitoring, reporting, or analytics capabilities.
Implementing Role-Based Access Control (RBAC)
Implementing role-based access control (RBAC) ensures that users only have access to the resources they need to perform their job functions. This enhances security by minimizing the risk of accidental or intentional misuse of privileges, while also simplifying user management and permissions.
Case Studies and Real-World Examples
Case Study: A Manufacturing Company's Journey
A leading manufacturing company implemented RemoteIoT desktop login to manage their IoT-enabled production line. By adopting best practices such as strong password policies and regular software updates, they successfully reduced downtime and improved overall efficiency. This case study demonstrates the tangible benefits of mastering RemoteIoT login in a real-world scenario.
Example: Enhancing Security in Healthcare
In the healthcare sector, RemoteIoT desktop login plays a critical role in managing medical devices and patient data. A hospital implemented multi-factor authentication and real-time monitoring to enhance security, resulting in a significant reduction in data breaches and improved patient care.
Future Trends in RemoteIoT Login
Emerging Technologies
Emerging technologies such as biometric authentication and blockchain are set to revolutionize RemoteIoT desktop login processes. Biometric authentication offers a secure and convenient way to verify user identity, while blockchain provides a decentralized and tamper-proof method for managing login credentials.
Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are increasingly being used to enhance RemoteIoT login security. These technologies can analyze user behavior patterns to detect anomalies and potential threats, providing proactive protection against cyber attacks.
Conclusion
In conclusion, mastering RemoteIoT desktop login is essential for anyone working with IoT technologies. By following the steps and best practices outlined in this guide, you can ensure secure and efficient access to your IoT ecosystem. Remember to regularly update your software, implement strong security measures, and stay informed about emerging trends to stay ahead of potential challenges.
We invite you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more insights into IoT and related technologies. Together, let's build a safer and more connected digital future!
Table of Contents