As technology continues to evolve, the demand for secure and efficient remote IoT (Internet of Things) access has grown significantly. If you're managing an IoT network behind a firewall using a Mac server, it's essential to understand the best practices and tools to ensure seamless connectivity while maintaining security. This guide will walk you through the process of using RemoteIoT behind a firewall with a Mac server.
RemoteIoT is a powerful solution for managing IoT devices remotely, even when they're located behind a corporate firewall. With the increasing number of IoT devices being deployed globally, ensuring secure access is critical. Whether you're managing home automation systems or industrial IoT devices, this guide will help you navigate the complexities of setting up a Mac server to handle remote IoT connections.
In this article, we'll explore step-by-step instructions, best practices, and troubleshooting tips to help you configure and use RemoteIoT effectively. By the end of this guide, you'll have a comprehensive understanding of how to set up a secure and reliable remote IoT environment using a Mac server.
Read also:5movierulz 2023 Download Your Ultimate Guide To Streaming And Downloading Movies
Table of Contents
- Introduction to RemoteIoT
- Overview of Mac Server
- Understanding Firewalls
- Step-by-Step Setup
- Security Measures for RemoteIoT
- Troubleshooting Common Issues
- Optimizing Performance
- Long-Tail Keywords and Variations
- Use Cases for RemoteIoT
- Conclusion
Introduction to RemoteIoT
RemoteIoT is a cutting-edge solution designed to facilitate remote management of IoT devices. It allows users to access and control IoT devices from anywhere in the world, even when these devices are located behind a corporate firewall. The platform supports a wide range of IoT protocols and ensures secure communication between devices and the central server.
Why Use RemoteIoT?
There are several reasons why organizations choose RemoteIoT for managing their IoT infrastructure:
- Security: RemoteIoT employs robust encryption and authentication mechanisms to protect data in transit.
- Scalability: The platform can handle large-scale IoT deployments without compromising performance.
- Flexibility: It supports various IoT protocols, making it compatible with a wide range of devices.
Overview of Mac Server
A Mac server is a powerful tool for managing networks, hosting services, and running applications. When used in conjunction with RemoteIoT, it can provide a secure and reliable platform for managing IoT devices behind a firewall. Mac servers are known for their stability, ease of use, and compatibility with a wide range of software.
Key Features of Mac Server
- Support for multiple users and devices
- Built-in security features
- Integration with Apple ecosystem
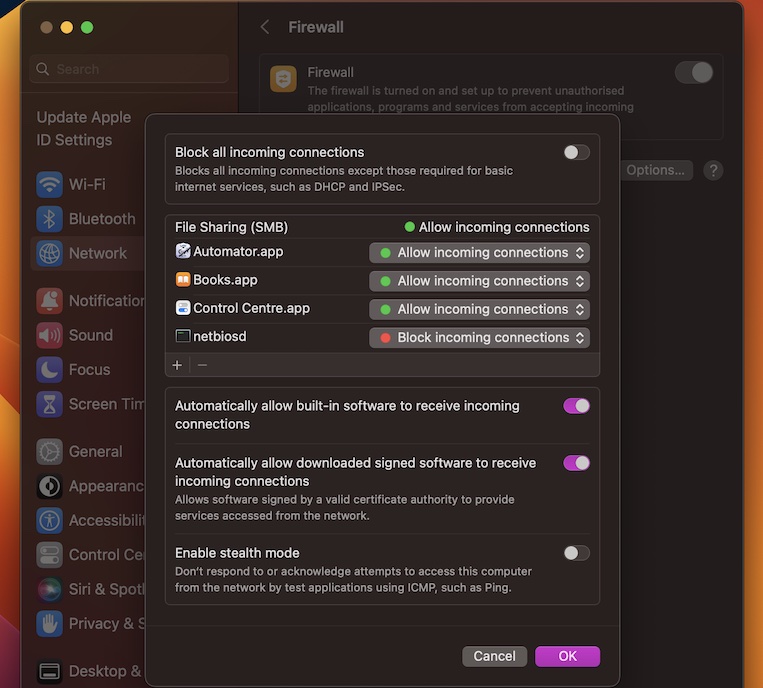
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls are essential for protecting IoT devices from unauthorized access and cyber threats. When setting up RemoteIoT behind a firewall, it's crucial to configure the firewall correctly to allow secure communication between devices and the server.
Types of Firewalls
- Packet Filtering Firewalls: Inspect individual packets and allow or block them based on rules.
- Stateful Inspection Firewalls: Track active connections and make decisions based on the context.
- Application-Level Gateways: Operate at the application layer to provide advanced filtering capabilities.
Step-by-Step Setup
Setting up RemoteIoT behind a firewall using a Mac server involves several steps. Below is a detailed guide to help you through the process:
Step 1: Install and Configure Mac Server
Begin by installing macOS Server on your Mac. Once installed, configure the necessary services such as file sharing, mail, and web hosting. Ensure that the server is updated with the latest security patches.
Read also:Best Securely Connect Remote Iot P2p Ssh Raspberry Pi Download
Step 2: Configure Firewall Rules
Adjust your firewall settings to allow traffic on the ports required by RemoteIoT. Common ports include 80 (HTTP), 443 (HTTPS), and any custom ports used by your IoT devices.
Step 3: Install RemoteIoT Software
Download and install the RemoteIoT software on your Mac server. Follow the installation instructions carefully to ensure proper setup.
Security Measures for RemoteIoT
Security is a top priority when managing IoT devices remotely. Below are some best practices to enhance the security of your RemoteIoT setup:
Use Strong Authentication
Implement multi-factor authentication (MFA) to protect against unauthorized access. Require users to provide two or more verification factors before granting access to the system.
Encrypt Data in Transit
Use secure protocols such as HTTPS and TLS to encrypt data transmitted between devices and the server. This ensures that sensitive information remains protected from eavesdropping and tampering.
Troubleshooting Common Issues
Even with careful planning, issues may arise during the setup process. Below are some common problems and their solutions:
Connection Problems
- Check firewall rules to ensure the necessary ports are open.
- Verify that the RemoteIoT software is properly installed and configured.
Optimizing Performance
To ensure optimal performance of your RemoteIoT setup, consider the following tips:
Monitor Network Traffic
Use network monitoring tools to track bandwidth usage and identify potential bottlenecks. This will help you optimize resource allocation and improve overall performance.
Long-Tail Keywords and Variations
In addition to the primary keyword "how to use remoteiot behind firewall using mac server," consider incorporating the following long-tail keywords:
- RemoteIoT configuration for Mac server
- Managing IoT devices behind firewall
- Secure remote access to IoT devices
Use Cases for RemoteIoT
RemoteIoT can be used in a variety of scenarios, including:
Home Automation
Control smart home devices such as thermostats, lights, and security systems from anywhere in the world.
Industrial IoT
Monitor and manage industrial equipment and processes remotely, improving efficiency and reducing downtime.
Conclusion
In conclusion, using RemoteIoT behind a firewall with a Mac server is a powerful solution for managing IoT devices securely and efficiently. By following the steps outlined in this guide, you can set up a robust and reliable remote IoT environment. Remember to prioritize security and regularly update your system to protect against emerging threats.
We invite you to share your thoughts and experiences in the comments section below. If you found this article helpful, please consider sharing it with others. For more insights into IoT management and cybersecurity, explore our other articles on the website.

![Mac Firewall Setting How To Configure It? [Stepwise Tutorial]](https://techyhost.com/wp-content/uploads/2022/12/changing-firewall-settings-mac-1.jpg)